In this fast-paced world of digital transformation, the internet has opened new avenues for connectivity. Information and services available to everyone at scale have also increased the chances of being misled or falling prey to internet shams. However, there is always a solution to avoid becoming a victim of scams and protect yourself and your devices from harm.
What is DomainKeys Identified Mail?
DomainKeys Identified Mail, also called DKIM, is a protocol that allows email authentication. DomainKeys Identified Mail(DKIM) protects email senders and recipients from receiving spam or falling prey to spoofing, and phishing. This form of email authentication helps organizations claim responsibility for messages in a way that the recipients can validate.
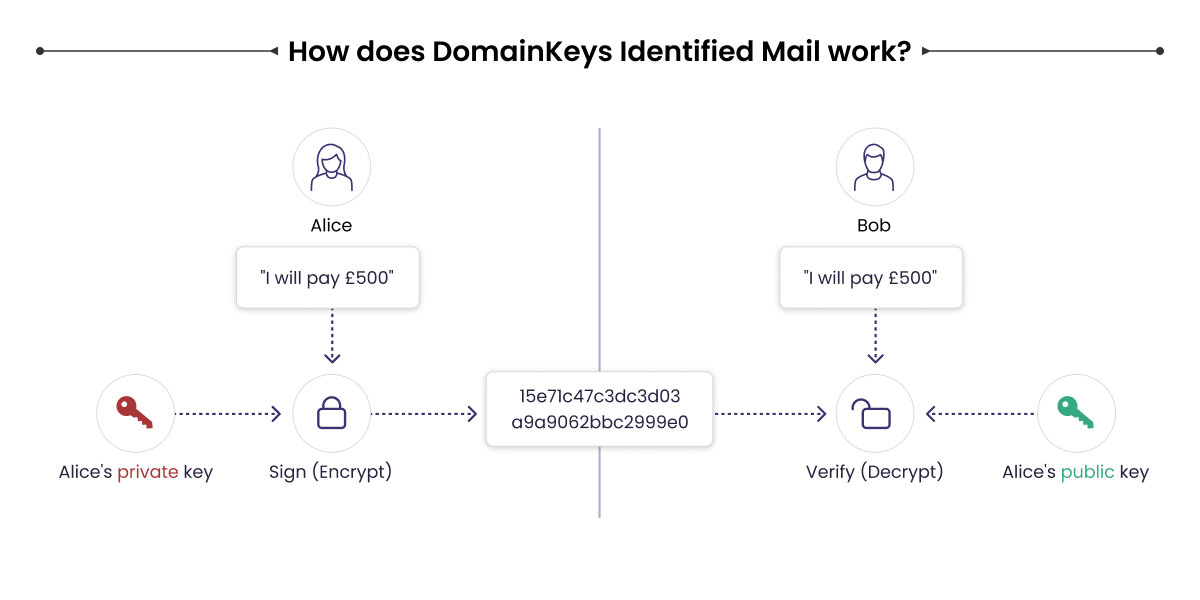
A DKIM signature is essentially a way of cryptographic authentication with an encrypted digital key. It is a prominent validation feature with a hash created by various components within the message. The sender can use the domain, the body of the message, and other parts to create a signature. Once these components are decided when the message is being sent, you cannot change it later. You can think of it as signing a crucial document with some invisible ink. This indicates that the message has come from you and no one else.
Why is DomainKeys Identified Mail important for businesses?
Email Marketing, even today, serves as an essential channel for user communication that brands leverage to develop deep, meaningful relationships with their customers. While brands have made an effort to gain customer trust and loyalty via email as a communication channel, some cyber criminals can take undue advantage of this situation.
This is done when these cyber criminals impersonate your brand’s emails and web pages to sneak their way into your inboxes. These scammers trick people into installing malware or sharing sensitive information with them. The sensitive information they give up could include their bank account details, social security numbers, credit card information, or any logins for online accounts. This scamming can easily lead to identity theft and hurt the recipients of such emails.
How does DomainKeys Identified Mail work?
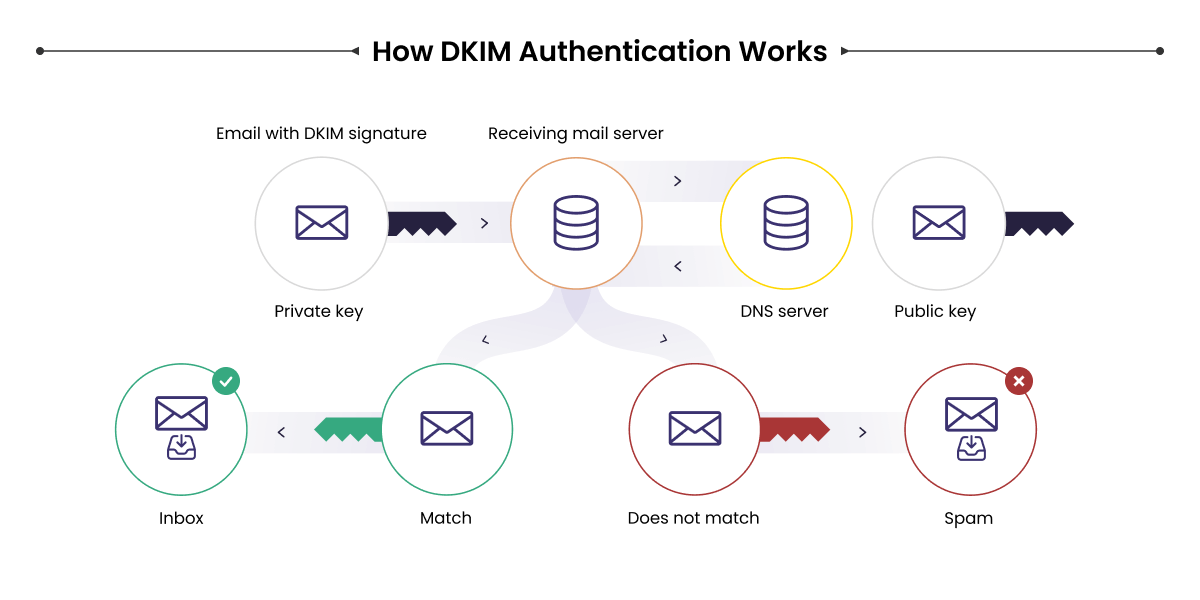
There are three steps to the DomainKeys Identified Mail (DKIM) signing process.
Step 1: The sender first identifies the fields they want to include in the DKIM signature. These fields in the signature include the “from” address of the sender, the body, the subject of the message, and others. Once decided, these fields must remain unchanged, or the DKIM authentication will fail.
Step 2: The sender’s email platform then creates a hash of the text fields included in the DKIM signature.
Once this hash string is generated, it is encrypted with a private key, which is only accessible to the sender.
Step 3: After the email is sent, it is up to the email gateway/consumer mailbox provider to validate the DKIM signature by finding the public key that perfectly matches the private key. The DKIM signature is then decrypted back to the original hash string.
Then, the receiver generates its hash of the fields included in the DKIM signature and compares it with the decrypted hash string. If both of these match, we can conclude that the DKIM signature fields have not been changed in transit and that the email’s sender truly owns the email received.
Encrypting your email messages with the DKIM signatures ensures that the recipients are safe and don’t fall prey to scams run by cyber criminals. Like DKIM, there are various frameworks for email authentication. One such is the Sender Policy Framework (SPF). Sender Policy Framework allows email senders to define which IP (Internet Protocol) addresses are allowed to send mail for a particular domain. DKIM, on the other hand, creates an encryption key and digital signature that helps verify that an email message was not forged or altered in transit.
Conclusion
A DKIM signature is essentially a way of cryptographic authentication with an encrypted digital key. It is a prominent validation feature with a hash created by various components within the message. It enables you to avoid becoming a victim of scams and protect yourself and your devices from harm. Learn more about your DKIM signature with WebEngage today. Sign up for out 14 day trial.